Description:
Memcached is an open-source, easy-to-use, high-performance, in-memory data store. It is a general-purpose distributed memory-caching system intended to speed up dynamic web applications by reducing the database load. It's used as a cache or session store. It is a popular choice for powering real-time applications in Web, Mobile Apps, Gaming, Ad-Tech, and E-Commerce.
Memcached is a Memcached-compatible in-memory key-value store service that can be used as a cache or a data store.
Security groups provide stateful filtering of ingress/egress network traffic to AWS resources. It is recommended that no security group allows unrestricted ingress access to Memcached port 11211.
Rationale:
Removing unfettered connectivity to remote console services, such as SSH, reduces a server's exposure to risk. Ensure no security groups allow ingress from 0.0.0.0/0 or::/0 to Memcached port 11211.
Impact:
For updating an existing environment, care should be taken to ensure that administrators currently relying on an existing ingress from 0.0.0.0/0 have access to Memcached port 11211 through another security group and also prevent the cache poisoning attack.
Default Value:
Memcached is running on the default port 11211.
The default value in the Security Group
Inbound
Type | Protocol | Port Range | Source | Description |
All traffic | All | All | Security Group ID | For the associated instances, inbound traffic allows network interfaces that are assigned to the same security group. |
Remediation:
The following steps to determine if the account is configured as prescribed:
Audit:
- log in to AWS Management Console and go to VPC https://console.aws.amazon.com/vpc/home

- Go on Security Groups in the left navigation

- To audit select all Security group one by which contain Memcached port 11211 in the inbound

- Click the Inbound Rules tab

- Ensure no rule exists that has a port range that includes Memcached port 11211 and has a Source of 0.0.0.0/0

Using AWS CLI
The following command describes a security group the command you can use for each security groups individual to check which IP or ports inbound or outbound
aws ec2 describe-security-groups --region us-east-1 --filters \
Name=ip-permission.from-port,Values=11210 Name=ip-permission.to-port,Values=11212 \
Name=ip-permission.cidr,Values='0.0.0.0/0' \
--query 'SecurityGroups[*].{Name:GroupName}'Remediation:
Pre-Requisites
- Before starting, the below implementation steps write all configurations which IP and which port in the inbound.
- Avoid the login through the Root user.
- Only authorized persons (i.e, admins) can access the Security Groups.
- You cannot delete the default security groups but you can edit and modify them here you can create security groups and create your own rules in them.
- Do not attach the default security group to any EC2 instance.
Implementation Steps
Perform the following steps to implement the prescribed state:
Step 1: Login to AWS Management Console and go to VPC https://console.aws.amazon.com/vpc/home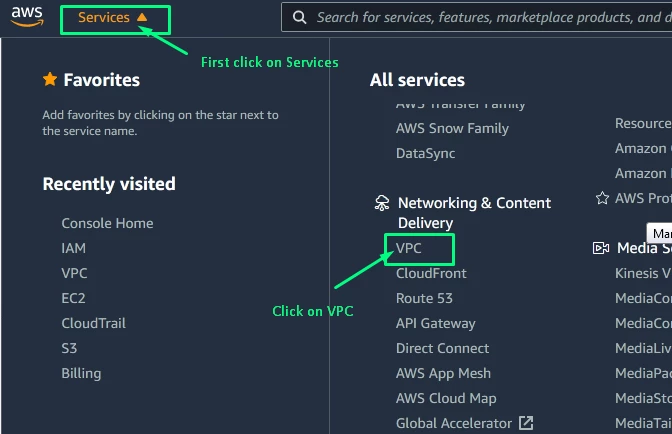
Step 2: Go on Security Groups in the left navigation. 
Step 3: For each security group, which contain Memcached port 11211 edits the rule and remove the CIDR 0.0.0.0/0 from inbound and assign the particular IP which you used : 
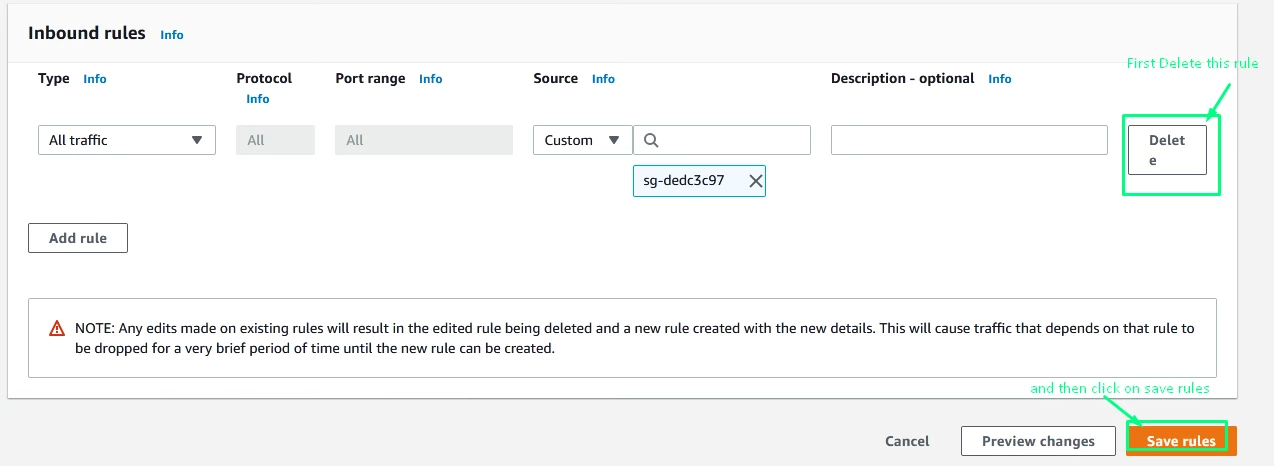
Step 4: Click on the Inbound Rules tab 
Step 5: Remove any rules that allow to inbound from 0.0.0.0/0 for port 11211 
Using AWS CLI
Remove the inbound rule(s) that permits unrestricted ingress to TCP port 11211 from the selected Security Group
aws ec2 revoke-security-group-ingress --region <region> \ --group-name <group_name> --protocol tcp --port 11211 --cidr 0.0.0.0/0
Optionally add a more restrictive ingress rule to the selected Security Group
aws ec2 authorize-security-group-ingress --region <region> \ --group-name <group_name> --protocol tcp --port 11211 --cidr <cidr_block>
Backout Plan:
If you want to proceed with previous settings go through the Implementation steps section and set all previous policies that you have written somewhere.
You can delete your new security group by following steps:
- Open the Amazon VPC console https://console.aws.amazon.com/vpc/

- In the navigation pane, choose Security Groups.

The above only for example please choose the security group which created by you do not select the default security group. and then click on Actions scroll down and click on Delete security groups we see in the below step. - Select one or more security groups and choose Security Group Actions, Delete Security Group.

- In the Delete Security Group dialogue box, choose Yes, Delete
or if any issue to access your port 11211 then assign the CIDR 0.0.0.0/0 in the inbound to the security group
Using AWS CLI
The following command is used to delete the created security group id in the security_group_id enter the security group id you show on your console.
aws ec2 delete-security-group --group-id <security_group_id>


