Description:
The storage account container that stores exported Azure Activity Logs must not be publicly accessible. Activity logs contain sensitive operational information such as authentication events, configuration changes, resource modifications, and administrative actions. If the container is publicly exposed, unauthorised users, including attackers, could download or analyse these logs. This could reveal valuable insights into the environment’s structure, security posture, and potential vulnerabilities.
Rationale:
Allowing public access to activity logs can unintentionally provide adversaries with visibility into the account’s activities, configurations, and potential weaknesses. Attackers can use this information to plan targeted attacks or locate misconfigurations. Restricting public access ensures that only authorised users with proper storage account permissions can access these critical logs.
Impact:
Setting the container Access Policy to Private removes public and anonymous access for all users except authorised storage account owners.
If access is required for specific users, shared access signatures (SAS), RBAC, or Azure AD permissions must be explicitly configured to allow controlled access.
Default Value:
By default, public access is set to null, meaning the container allows only private access. The activity log export container is not publicly accessible unless manually changed.
Test plan:
Sign in to the Azure Portal at https://portal.azure.com
Search for Storage Accounts
Open the Storage Account used for Activity Log export
Under Data storage, select Containers
Select the container used for storing Activity Logs
Verify the Public access level is set to Private.
If public access is enabled, follow the implementation steps
Implementation steps:
Sign in to the Azure Portal at https://portal.azure.com
Search for Storage Accounts and select the storage account.
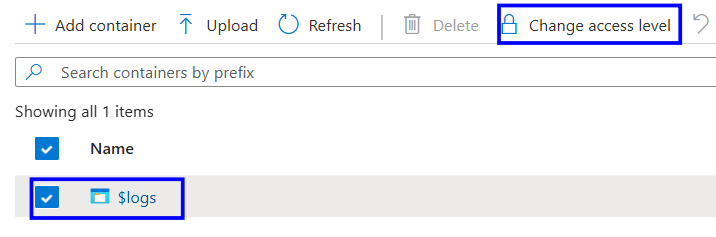
Under data storage, click on containers and select the container used for storing logs.
Select the container used for storing logs and click Change Access Level.
Set the Public access level to Private (no anonymous access)
Save the changes
Backout Plan:
Sign in to the Azure Portal at https://portal.azure.com
Search for Storage Accounts
Open the Storage Account and under the data storage, click the container
Modify Public Access Level back to the previous configuration if operationally required
Save the changes
References: