Description:
Azure Network Security Groups (NSGs) enforce network filtering rules for virtual machines, subnets, and other Azure resources. Deleting an NSG instantly removes all associated network protections, which can expose workloads to unauthorized access or lateral movement. Activity Log Alerts must be configured to detect NSG deletion events so that security teams are notified immediately and can investigate potentially harmful or unexpected actions. This control verifies that an Activity Log Alert exists to monitor delete operations for NSGs.
Rationale:
This rule checks whether an Activity Log Alert monitors the operation of Microsoft.Network/networkSecurityGroups/delete. If such an alert does not exist, the configuration is considered NON_COMPLIANT. Deleting an NSG is a high-risk action because it removes all security filtering for attached resources. Without monitoring, unauthorized NSG deletions can go unnoticed, leading to exposure of internal resources, compliance violations, and an increased attack surface.
Impact:
Enables real-time detection of NSG deletion events.
Supports incident response, change auditing, and forensics.
Helps enforce change-control policies for network configurations.
Contributes to compliance with frameworks such as CIS, NIST, PCI, etc., which require monitoring of security control changes.
Default Value:
Azure does not automatically create or enforce Activity Log Alerts for NSG deletion. Administrators must configure them manually in Azure Monitor.
Pre-Requisites:
Owner, Contributor, or Monitoring Contributor on the subscription or resource group.
Permissions to manage alerts and action groups of Microsoft.Insights/activityLogAlerts/write, Microsoft.Resources/subscriptions/resourceGroups/read, Microsoft.Network/networkSecurityGroups/read
Test Plan:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to Monitor
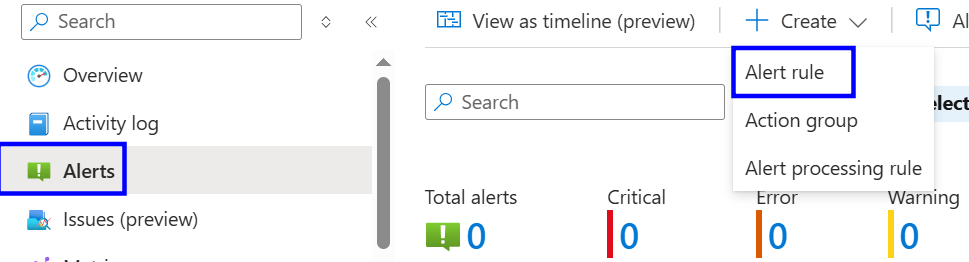
Select Alerts
Open Alert rules
Verify an Activity Log Alert exists for "Delete Network Security Group (Network Security Group)"
Verify the alert scope includes the required subscription
Verify that an Action Group is associated
If the alert does not exist, follow the implementation steps
Implementation Steps:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to Monitor
Select Alerts
Click Create and select Alert rule
Set the Scope to the required subscription
Under Condition, click See all signals, search for "Delete Network Security Group (Network Security Group)", and select the signal.
Associate with an Action Group
Provide an alert rule name
Click Review + Create
Click Create
Backout Plan:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to Monitor
Select Alerts
Open Alert rules
Locate the "Delete Network Security Group" Activity Log Alert
Delete the alert rule
Confirm the deletion
Reference:
https://learn.microsoft.com/azure/azure-monitor/alerts/activity-log-alerts
https://learn.microsoft.com/rest/api/monitor/activitylogalerts
https://learn.microsoft.com/azure/security/benchmarks/security-controls-v3-logging-threat-detection