Description:
This control ensures that Azure SQL Servers do not allow access from all IP addresses (0.0.0.0/0). Allowing access from any IP would expose the database to the public internet and increase the risk of unauthorized access. To reduce this risk, firewall rules must restrict access to specific, trusted IP addresses or approved virtual networks while preventing unrestricted internet access.
Rationale:
Azure SQL Server has a firewall that blocks unauthorized connections.
Using specific IP ranges or service endpoints reduces the attack surface.
Prevents exposure of sensitive data and mitigates potential attacks, such as brute-force login attempts and SQL injection.
Helps meet security and compliance best practices.
Impact:
Restricting access may break connections from clients or services that were previously using public access.
To maintain connectivity, you must define custom firewall rules for trusted IPs or enable virtual network/service endpoint access.
Default Value:
By default, Azure SQL Server does not allow access from all IP addresses. Only Azure services are allowed, and public internet access from ANY IP (0.0.0.0/0) is not enabled by default.
Pre-requisites:
An existing Azure SQL Server
Permissions: Owner, Contributor, or SQL Server Contributor
Test Plan:
Sign in to the Azure Portal at https://portal.azure.com
Go to SQL Servers
Select the SQL Server hosting the database
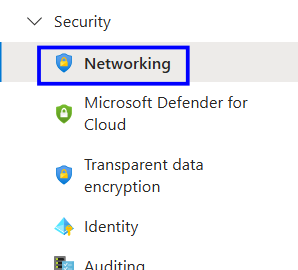
Under settings, Open Networking
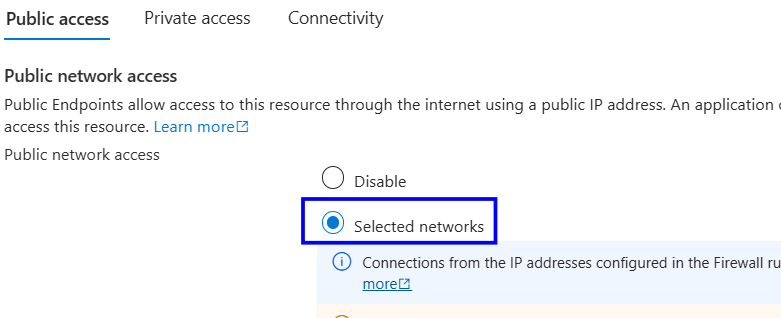
Verify Public network access is Disabled
ORIf set to Selected networks, verify that no firewall rule allows
0.0.0.0 – 255.255.255.255 (ANY IP)If not, follow the implementation steps.
Implementation Steps:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to SQL Servers
Select the Azure SQL Server that hosts the database
In the left-hand menu, under security, select Networking
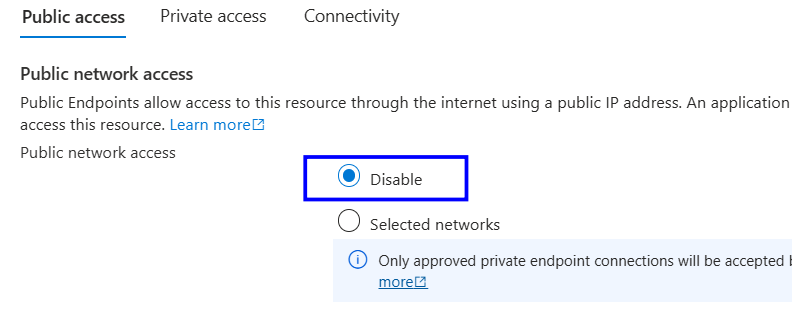
Under Public network access, select Disabled
Click Save
Backout Plan:
Log in to the Microsoft Azure Portal https://portal.azure.com
Navigate to SQL Servers
Select the Azure SQL Server hosting the database
In the left-hand menu, select Networking
Under Public network access, select Selected networks
Add firewall rules for the required trusted IP addresses
Click Save
References: