Description:
Transparent Data Encryption (TDE) protects SQL databases at rest. By default, SQL uses a Microsoft-managed key to encrypt the TDE protector. Changing the protector to a Customer-Managed Key (CMK) stored in Azure Key Vault gives you full control over the encryption key used to protect SQL data.
Rationale:
Using a customer-managed key improves security by allowing full control over key rotation, access policies, disabling, and revocation. This helps meet compliance requirements and provides better assurance that only authorized users and services can use the TDE protector.
Impact:
Using CMKs requires proper Key Vault access policies.
If the key is deleted, disabled, or access is removed, SQL databases may become unreadable. Key management must be handled carefully to avoid service disruption.
Default Value:
By default, SQL servers use Microsoft-managed keys for TDE encryption.
Pre-requisites:
You must have an Owner, Contributor, or SQL Security Manager role.
An Azure Key Vault must exist.
A key must be created or imported into the Key Vault.
The SQL server must be granted access to the Key Vault.
Test Plan:
Sign in to the Azure portal at https://portal.azure.com.
In the portal, search for SQL servers.
Select the SQL server you want to review.
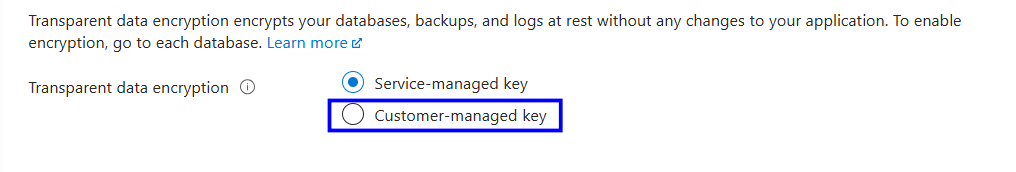
Under the Security section, select Transparent data encryption.
Check the Transparent data encryption
Confirm that the Customer-managed key is selected.
If it shows a Service-managed key, follow the implementation plan.
Implementation Plan:
Open the Azure portal at https://portal.azure.com.
Create a new Azure Key Vault or use an existing one.
Create or import a key in the Key Vault.
In the portal, search for the SQL server you want to configure.
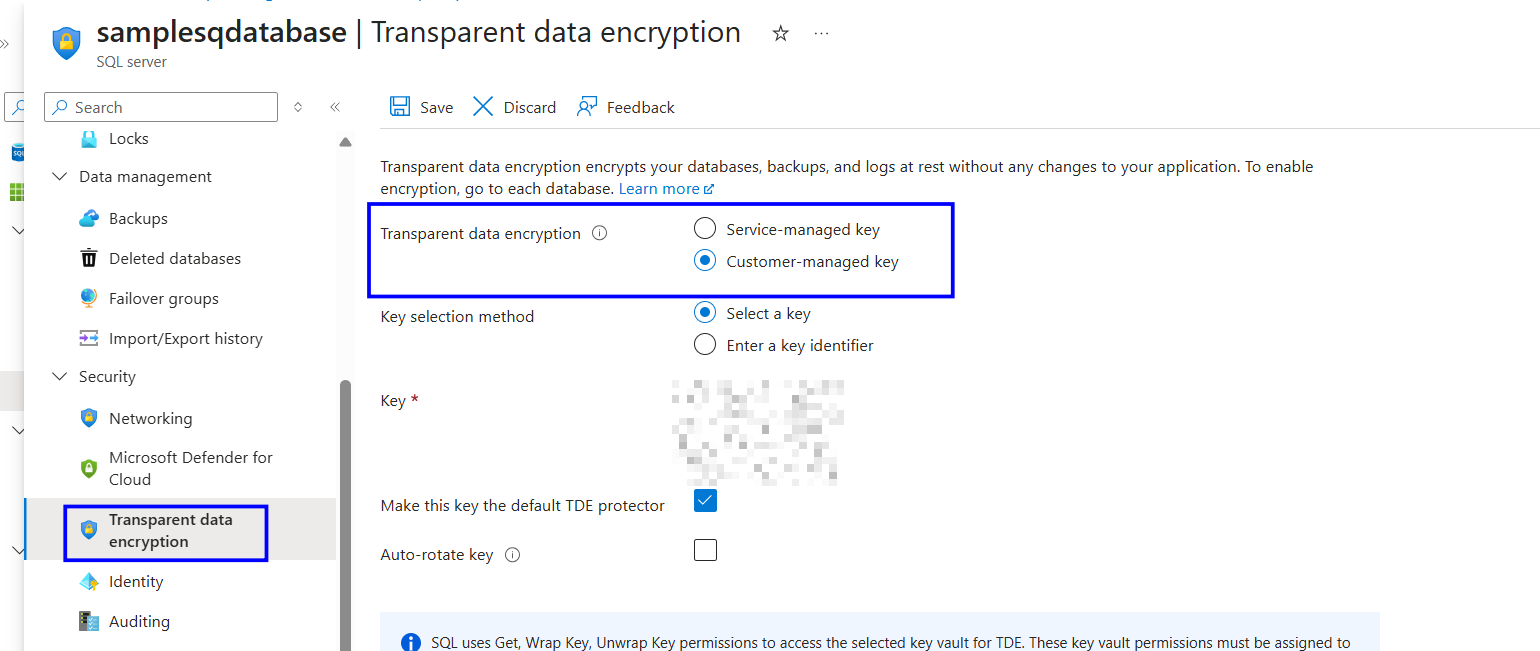
Under the Security section, select Transparent data encryption.
Select Customer-managed key. In the Key selection method, choose Select a key.
Choose the Key Vault, Key, and Key Version.
Save the configuration.
Backout Plan:
Open the Azure portal at https://portal.azure.com.
In the portal, search for SQL servers and open the SQL server you want to modify.
Under the Security section, select Transparent data encryption.
Change the encryption type back to Service-managed key.
Click Save to apply the changes.
Reference: