Description:
Azure Web Apps allow administrators to enforce a minimum TLS version for all HTTPS traffic. Setting the Minimum TLS Version to 1.2 or higher ensures secure, encrypted communication between clients and the application.
Rationale:
Older TLS versions, such as 1.0 and 1.1, are insecure and vulnerable to modern attacks. Enforcing TLS 1.2 or higher ensures stronger encryption for data in transit and aligns with current security and compliance standards, providing better protection against unauthorized access and exploits.
Impact:
Clients that do not support TLS 1.2 or above will fail to connect. Confirm client compatibility before upgrading.
Default Value:
New Web Apps default to TLS 1.2.
Older Web Apps may still use TLS 1.0 or 1.1.
Pre-requisites:
You need an Owner, Contributor, or Website Contributor role.
All connecting applications must support TLS 1.2+.
Test Plan:
Sign in to the Azure portal at https://portal.azure.com.
In the portal, search for App Services and select the Web App.
Under Settings, select Configuration.
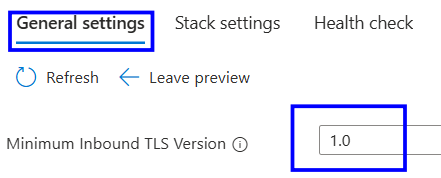
In the General settings tab and locate the Minimum TLS Version setting.
Verify that it is set to 1.2.
If it is set to 1.0 or 1.1, follow the implementation Steps.
Implementation Steps:
Sign in to Azure Portal: https://portal.azure.com
In the portal, search for App Services and select the Web App.
Under Settings, select Configuration.
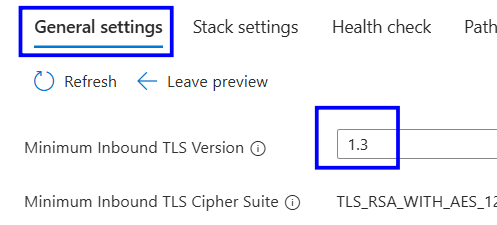
In the General settings tab, locate the Minimum TLS Version setting and change it to 1.2.”
Save changes.
Backout Plan:
Sign in to the Azure portal at https://portal.azure.com.
In the portal, search for App Services and select the Web App.
Under Settings, go to Configuration, then open the General settings tab.
Set the Minimum TLS Version back to the previous value (e.g., 1.1 or 1.0).
Click Save to apply the changes.
Reference:
https://learn.microsoft.com/azure/app-service/configure-ssl-bindings
https://learn.microsoft.com/azure/security/fundamentals/tls-certificate-management