Description:
The log_disconnections server parameter in PostgreSQL controls whether the database logs successful client disconnections. Enabling this parameter allows database administrators to track when sessions are terminated, providing a complete audit trail of database connections alongside log_connections. This is critical for auditing, security monitoring, and troubleshooting Azure PostgreSQL Database Servers (Single or Flexible).
Rationale:
Security Monitoring: Complements log_connections by providing a full session lifecycle, helping detect abnormal session terminations or unauthorized access patterns.
Audit & Compliance: Supports regulatory and internal auditing requirements by maintaining records of all connection/disconnection events.
Troubleshooting: Useful for diagnosing session-related issues and unexpected application disconnects.
Impact:
Full visibility into connection lifecycle events for compliance and operational monitoring.
Supports security audits and incident investigations.
Enhances troubleshooting capabilities for session-related problems.
Increases log volume, especially in high-traffic environments; proper log rotation and storage management are required.
Minimal performance overhead for logging disconnections; typically negligible in Azure-managed PostgreSQL.
Default Value:
For Azure Database for PostgreSQL Flexible Server, log_disconnections is ON by default
Pre-requisites:
Global Administrator or Security Administrator permissions.
Must be Azure Database for PostgreSQL – Flexible Server (or Single Server if the parameter is supported).
Test Plan:
Sign in to the Azure Portal at https://portal.azure.com
Search for and open the Azure Database for PostgreSQL server
Select the target PostgreSQL server
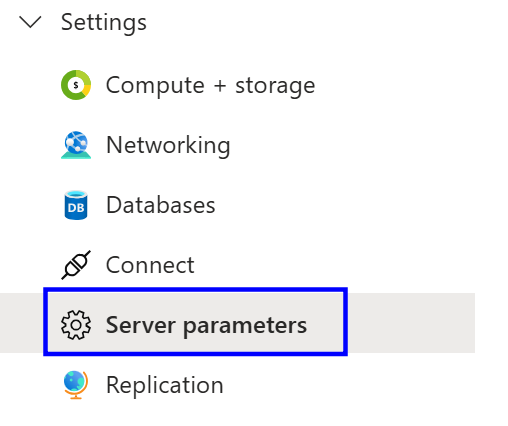
From the left menu, under settings, select Server parameters
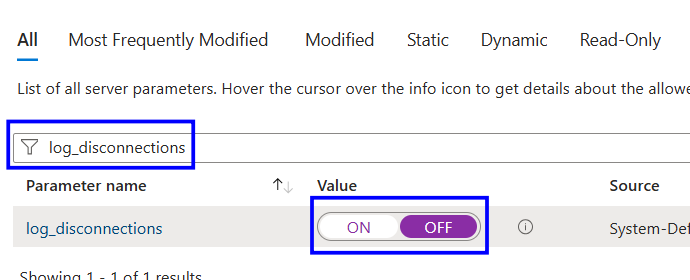
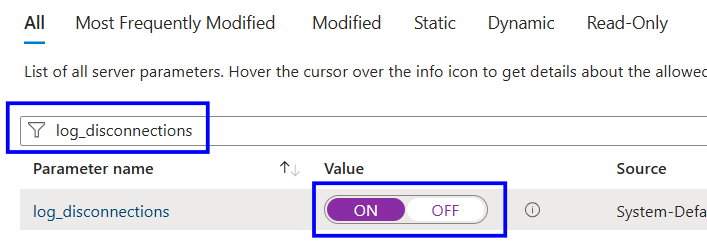
Search for the parameter log_disconnections
Verify log_disconnections is set to ON
If log_disconnections is not set to ON, follow the implementation steps
Implementation Steps:
Sign in to the Azure Portal at https://portal.azure.com
Search for your Azure Database for PostgreSQL server.
On the left-hand menu, under the Settings section, select server parameters.
Search for log_disconnections.
Set the value to ON
Save the changes.
Backout Plan:
Log in to the Azure Portal.
Search for your Azure Database for PostgreSQL server (Single or Flexible).
On the left-hand menu, under the Settings section, select server parameters.
Search for log_disconnections.
Set the value to OFF.
Save the changes.
Reference: