Description:
The Azure Database for PostgreSQL server includes a firewall option called “Allow access to Azure services”. When enabled, this setting allows all Azure-hosted services across all tenants to bypass firewall rules and connect to the PostgreSQL server. This setting effectively broadens the attack surface by allowing connections from any resource within the Azure cloud, not just the customer’s own subscriptions.
Rationale:
Enabling this setting introduces a high risk of unauthorized access because any Azure-based resource—potentially controlled by other customers—could attempt to authenticate to the PostgreSQL server.
Disabling the setting ensures that:
Only explicitly defined IP addresses and VNets may connect.
Network access is predictable and controlled.
Connections are limited to private and trusted network channels.
Impact:
Reduces attack surface.
Improves auditing and compliance posture.
Ensures connections are limited to trusted network locations.
Applications using public Azure service IPs or unmanaged PaaS services may lose connectivity if firewall rules or private endpoints are not correctly configured.
Default Value:
For Azure Database for PostgreSQL (Single Server and Flexible Server), the default state for Allow access to Azure services is Disabled, meaning broad-access firewall rules are not automatically created unless explicitly enabled.
Pre-requisites:
Global Administrator or Security Administrator permissions.
Test Plan:
Log in to the Azure Portal: https://portal.azure.com
Search for your Azure Database for PostgreSQL server Single or Flexible).
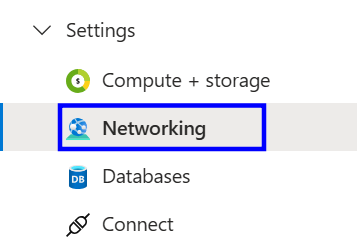
On the left-hand side, under the settings section and click on networking.
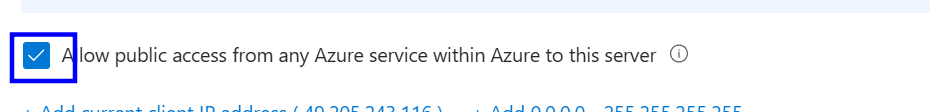
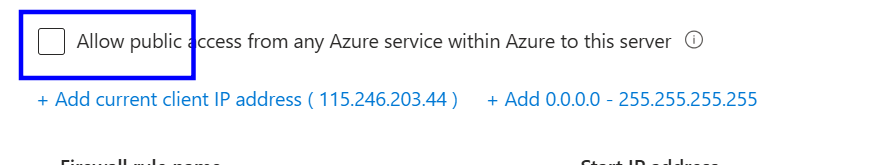
Check whether 'Allow public access from any Azure service within Azure to this server' is checked or not.
If the ‘Allow public access from any Azure service within Azure to this server' is checked, follow the implementation steps.
Implementation Plan:
Log in to the Azure Portal: https://portal.azure.com
Navigate to your PostgreSQL server (Single or Flexible).
Scroll down to security and click on networking.
In the Networking section, we need to uncheck 'Allow public access from any Azure service within Azure to this server.'
Save the changes.
Backout Plan:
Log in to the Azure Portal: https://portal.azure.com
Navigate to your PostgreSQL server (Single or Flexible).
Scroll down to security and click on networking.
In the Networking section, we need to check the Allow public access from any Azure service within Azure to this server.
Save the changes.
Reference: