Description:
Infrastructure double encryption adds an encryption layer on top of the default Azure Storage encryption for PostgreSQL Flexible Servers. With this feature enabled, data is encrypted twice using two separate encryption algorithms and two independent key sets. This provides enhanced data protection, meeting high-security and regulatory requirements for sensitive workloads. Double encryption ensures data remains protected even if one encryption layer is compromised.
Rationale:
Dual encryption strengthens the confidentiality of database storage by enforcing defense-in-depth at the infrastructure layer. It protects sensitive data from advanced threats, reduces exposure in case of key compromise, and helps satisfy strict compliance mandates such as financial, government, and regulated industry standards. Without double encryption, PostgreSQL relies only on the default single encryption layer, which may not meet elevated regulatory requirements.
Impact:
Enabling double encryption increases the security posture of PostgreSQL servers. However, it must be configured at server creation and cannot be enabled afterward, requiring recreation of the server if not initially set.
Default Value:
Infrastructure double encryption is Disabled by default.
Pre-Requisites:
PostgreSQL Server (double encryption not supported on a Single Server)
Encryption must be configured during server creation
Appropriate permissions to deploy PostgreSQL servers
Test Plan:
Sign in to the Azure Portal at https://portal.azure.com
Search for Azure Database for PostgreSQL – Flexible Server
Select the target PostgreSQL server
From the left menu, open Data encryption
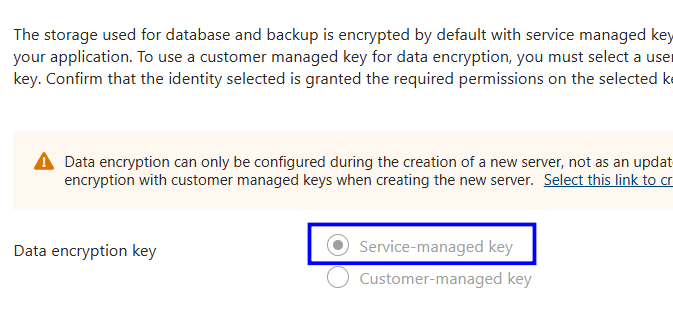
Review the Data encryption key configuration
Verify Customer-managed key is selected, indicating Infrastructure Double Encryption is enabled
If double encryption is not enabled, follow the implementation steps
Implementation Steps:
Sign in to the Azure Portal at https://portal.azure.com
Search for Azure Database for PostgreSQL – Flexible Server
Select Create to deploy a new PostgreSQL server
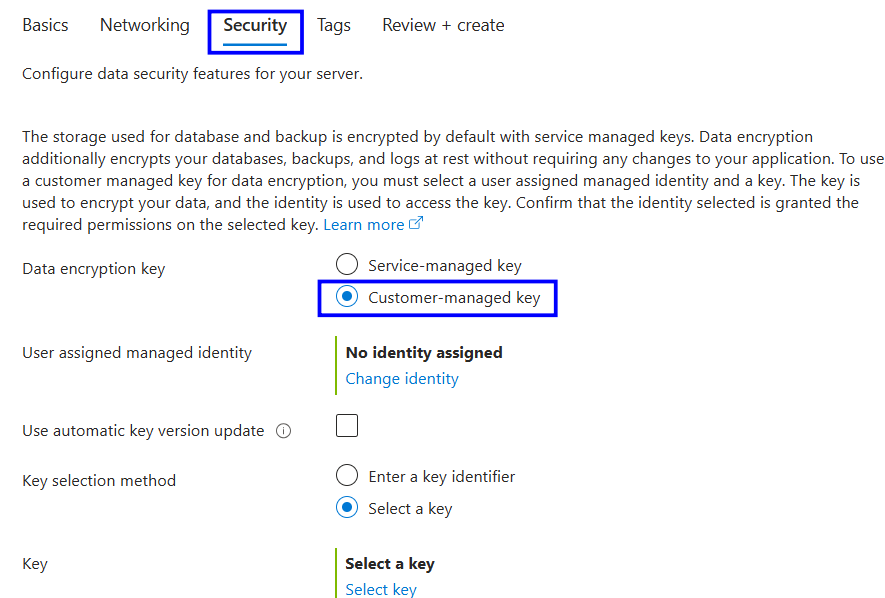
During server creation, navigate to the Data encryption section
Under security, select Customer-managed key
Choose the User-assigned managed identity
Select the Azure Key Vault and encryption key
Complete the remaining configuration and create the server
Backout Plan:
Sign in to the Azure Portal at https://portal.azure.com
Restore data to a new PostgreSQL server
During server creation, select Service-managed key under security.
Complete the server creation process
Reference:
https://learn.microsoft.com/azure/postgresql/flexible-server/concepts-security
https://learn.microsoft.com/azure/security/fundamentals/encryption-double