Description:
This control ensures that HTTP request and response logs are enabled for Azure App Services to capture web server activity. HTTP logs help administrators monitor traffic patterns, diagnose issues, detect suspicious behavior, and support auditing and forensic analysis.
Rationale:
HTTP logs provide visibility into application access and errors. Without them, troubleshooting incidents, detecting abuse, or performing investigations becomes difficult. Enabling logs ensures traceability and supports security monitoring and operational troubleshooting.
Impact:
Enabling HTTP logs may increase storage usage and generate additional data. There is no performance impact on the application, but log retention policies should be configured to control storage cost and volume.
Test Plan:
Sign in to the Azure Portal.
Go to App Services.
Select the Web App you want to audit.
On the left pane under Monitoring, click on Diagnostic settings.
Check that diagnostic settings are enabled for HTTP.
If not enabled, follow the implementation steps
Implementation Steps:
Sign in to the Azure portal: https://portal.azure.com
Search for the App Services and select the app services.
On the left pane under the monitoring section, click on Diagnostic settings.
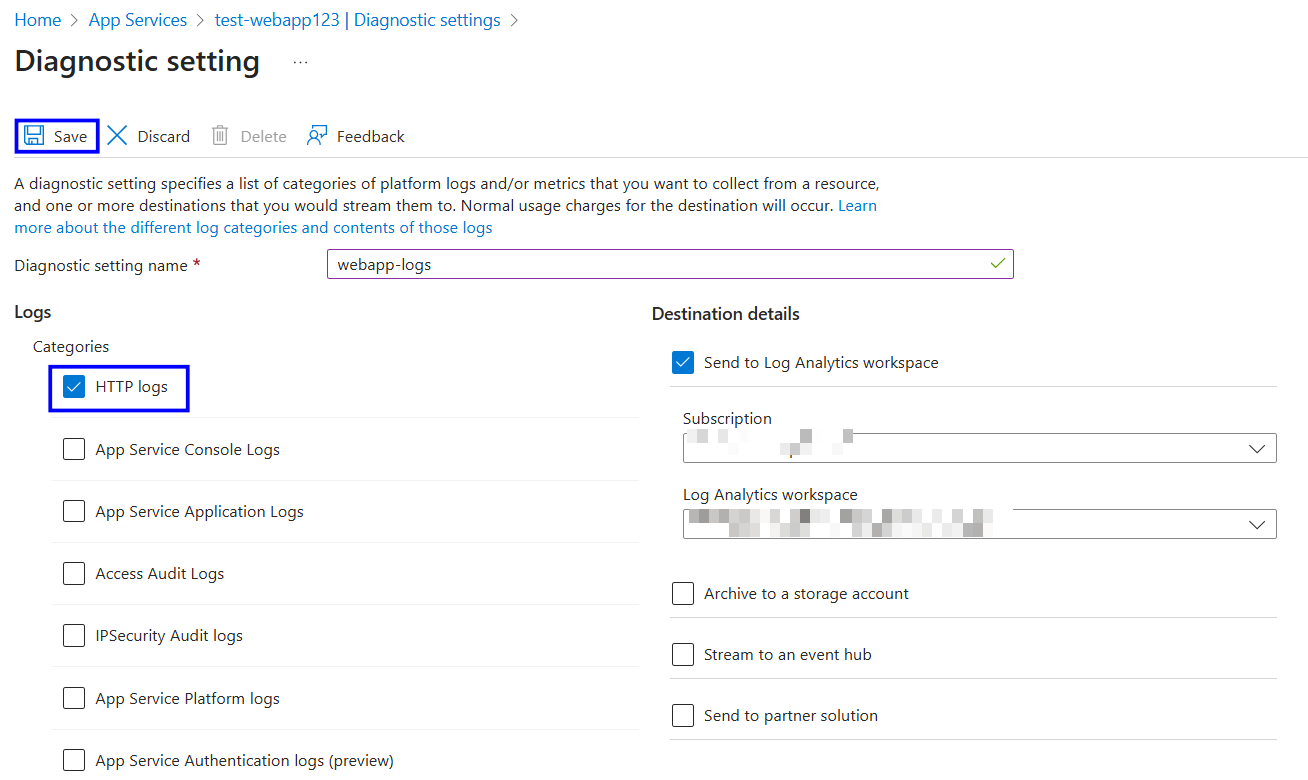
Click on Add diagnostic settings.
Provide a meaningful name for the diagnostic settings.
Under Log categories, select HTTP, and under Destination details, choose the storage account or log analytics workspace where you want the logs to be stored.
Save the changes.
Backout Plan:
Log in to Azure Portal: https://portal.azure.com
Search and select App Services from the portal menu.
Click the App Service where HTTP logs were enabled.
Go to Monitoring and select diagnostic settings, and select the diagnostic settings for HTTP.
References:
https://learn.microsoft.com/en-us/azure/app-service/troubleshoot-diagnostic-logs
https://learn.microsoft.com/en-us/azure/app-service/troubleshoot-diagnostic-logs#log-file-types
https://learn.microsoft.com/en-us/azure/azure-monitor/platform/diagnostic-settings