Description:
Azure Security Solutions include integrated services such as endpoint protection, vulnerability scanners, SIEM connectors, and third-party security tools managed through Microsoft Defender for Cloud. Deleting any of these solutions can remove essential security monitoring or protection. This control ensures an Activity Log Alert is configured to detect the deletion of a security solution so that security teams receive immediate notification of this high-impact change.
Rationale:
This rule validates the presence of an Activity Log Alert that monitors the operation Microsoft.Security/securitySolutions/delete. If this alert does not exist, the environment is considered non-compliant because the deletion of a security solution can disable key defenses, reduce visibility, and increase the risk of unauthorized changes going unnoticed. Monitoring such actions is required for strong security governance and aligns with compliance frameworks that mandate tracking changes to critical security controls.
Impact:
Ensures rapid detection of the deletion of critical security controls.
Helps identify insider threats or compromised administrator accounts.
Strengthens compliance posture by providing an audit trail of security configuration changes.
Supports security operations and forensics investigations.
Default Value:
Azure does not create Activity Log Alerts for Security Solution deletions by default. Administrators must manually configure alerts to monitor these events.
Pre-Requisites:
Azure subscription with permissions:
Microsoft.Insights/activityLogAlerts/write
Microsoft.Security/securitySolutions/read
Microsoft.Resources/subscriptions/resourceGroups/read
A defined Action Group for notifications (email/SMS/Teams/webhook/etc.)
Test Plan:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to Monitor
Select Alerts
Open Alert rules
Verify an Activity Log Alert exists for Delete Security Solution
Verify the alert scope includes the required subscription
Verify that an Action Group is associated
If the alert does not exist, follow the implementation steps
.
Implementation Steps:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to Monitor
Select Alerts
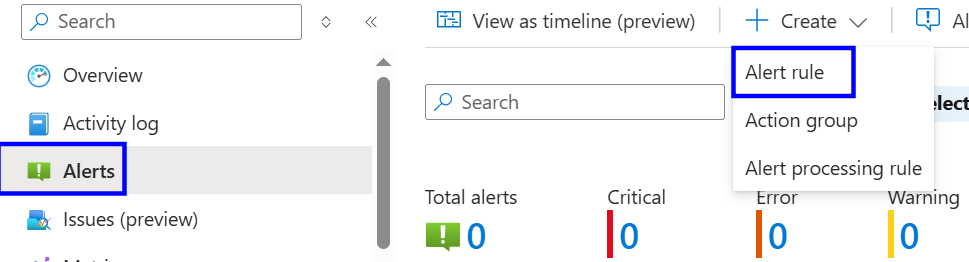
Click Create and select Alert rule
Set the Scope to the appropriate subscription
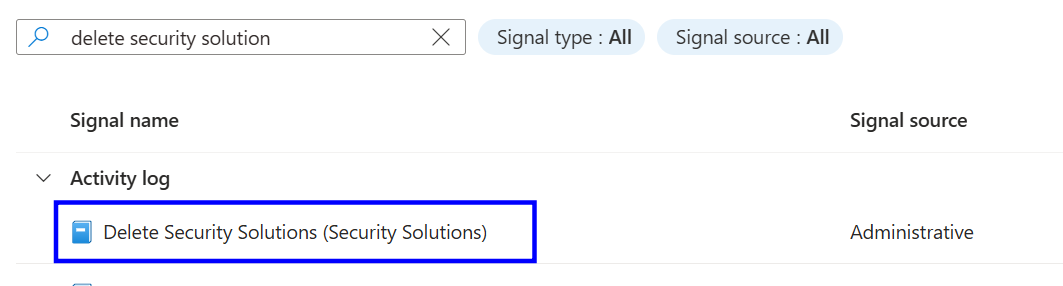
Under Condition, click See all signals, search for Delete Security Solution, and select the signal.
Associate with an existing Action Group or create a new one
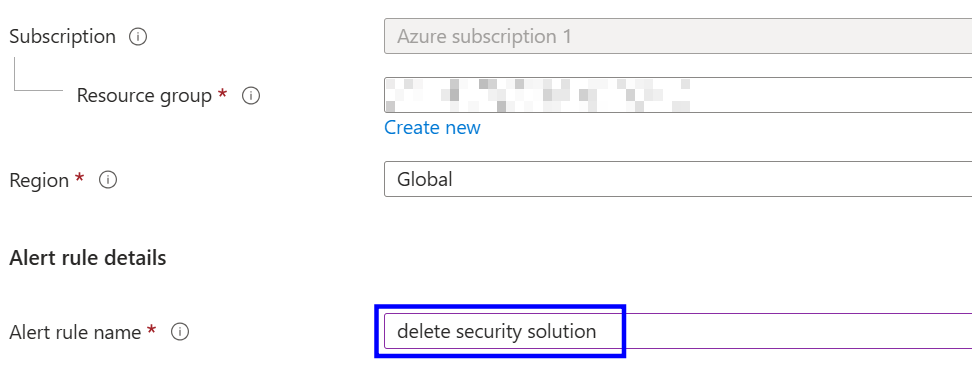
Provide an alert rule name and resource group
Open the Details
Click Review + Create
Click Create
Backout Plan:
Sign in to the Azure Portal at https://portal.azure.com
Navigate to Monitor
Select Alerts
Open Alert rules
Locate the Delete Security Solution Activity Log Alert
Delete the alert rule
Confirm the deletion
Reference:
https://azure.microsoft.com/updates/classic-alerting-monitoring-retirement
https://learn.microsoft.com/azure/azure-monitor/alerts/alerts-activity-log