Description:
SSH (Secure Shell) is used to remotely manage Linux-based virtual machines. Allowing SSH (port 22) to be accessed directly from the internet exposes VMs to brute-force attacks, credential guessing, and exploitation of SSH vulnerabilities. Restricting SSH access ensures only trusted and approved networks can connect. This can be enforced using Network Security Groups (NSGs) and Just-in-Time (JIT) VM Access to minimize exposure and reduce the attack surface.
Rationale:
Unrestricted SSH access from the internet enables attackers to attempt unauthorized login attempts and automated credential attacks. By restricting SSH to trusted IP ranges or enabling JIT access, organizations significantly reduce exposure to lateral movement, remote compromise, and unauthorized access. This control ensures SSH is not open to “Any / 0.0.0.0/0,” which is a major security risk.
Impact:
Restricting SSH improves VM security and reduces the attack surface. However, administrators must ensure that approved IPs or JIT access are configured correctly to avoid accidental denial of legitimate access. Proper planning ensures operational continuity while maintaining strong access controls.
Default Value:
By default, SSH (port 22) may be open to the internet unless restricted by NSG rules or JIT access settings.
Pre-requisites:
Network Security Groups (NSGs)
Azure Virtual Machines (VMs) with SSH enabled (typically on port 22).
Just-in-Time (JIT) VM Access should be enabled for additional control over SSH access.
Owner, Contributor, or Network Contributor role permissions.
Test Plan:
Sign in to the Azure Portal https://portal.azure.com
Open Network Security Groups.
Select the NSG associated with the Linux VM or subnet.
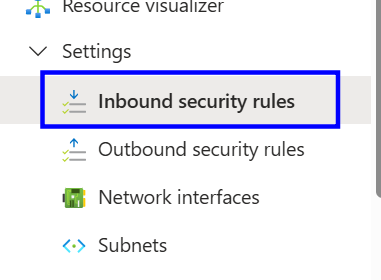
Under Settings, open Inbound security rules.
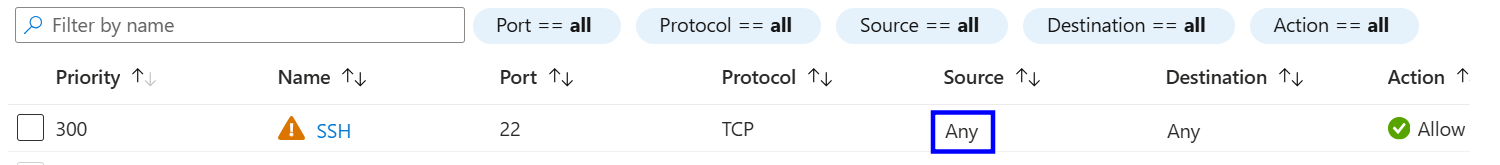
Review rules for TCP port 22 (SSH).
Confirm there is no rule allowing SSH from Any or 0.0.0.0/0.
If SSH is open to any, follow the implementation steps.
Implementation Steps:
Sign in to the Azure Portal
Open Network Security Groups.
Select the NSG associated with the VM.
Under Settings, open Inbound security rules.
Identify any rule allowing TCP port 22 (SSH) from Any or 0.0.0.0/0.
Remove or modify those rules.
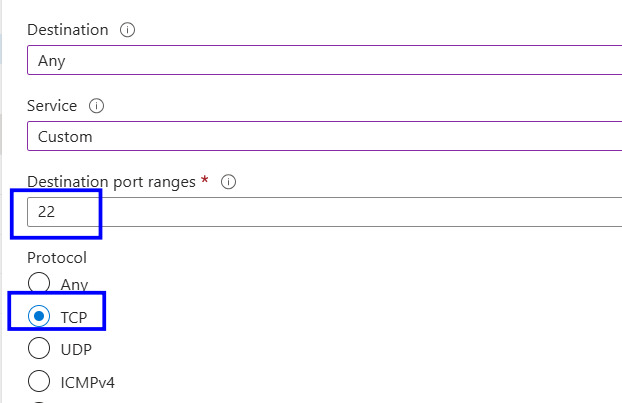
Add or update an inbound rule to allow SSH only from trusted IP addresses or private network ranges.
Ensure the rule uses:
Protocol: TCP
Destination port: 22
Save the changes.
Backout Plan :
Sign in to the Azure Portalhttps://portal.azure.com
Open Network Security Groups.
Select the NSG associated with the virtual machine.
Under Settings, open Inbound security rules.
Locate the SSH (TCP port 22) rule.
Modify the rule to restore the previous access configuration if required.
Save the changes
References: